Table of Contents (click to expand)
Satellite Internet is a type of Internet connectivity that uses satellites in space to provide Internet service to users on the ground. Satellite Internet can be used in areas where other types of Internet connectivity, such as broadband or DSL, are not available. Satellite Internet works by sending a signal from a satellite in space to a dish on the ground, which is then sent to a modem and then to the user’s computer.
In the 21st century, the Internet is ubiquitous, to the extent that some writers vehemently believe that access to it – the most capacious library of information in human history – must be a birthright. However, optical fibers cannot be slid everywhere; they require additional infrastructure to be drawn from. Rural areas still lack high-quality Internet for this very reason. However, satellite Internet, the so-called “wave of the future”, might change all of this.
Satellite Internet doesn’t require a multistory base station, but only a small, parabolic antenna dish that communicates wirelessly with a satellite above Earth’s equator. Of course, it’s always easier said than done.
Recommended Video for you:
Ka-Band Signals
The days when the Internet was merely used to exchange emails are long behind us. Only two decades ago, the ports were scarce and the ships carrying the goods between them were limited. Today, the ports are in the billions and the ships are unlimited. The Internet is the busiest network on the planet. To describe the commodities being traded as copious is a massive understatement. Last year, it is estimated that an unfathomable 11 exabytes of data was exchanged on the Internet. For perspective, 1 exabyte (EB ) is equal to 1,073,741,824 gigabytes (GB).

What opened the floodgates was the introduction of more applications. The Internet is no longer just an instant post office; it also houses entire shopping malls, markets, social meets, blind dating venues, and bookstores. However, the most recent additions are the most taxing: high-definition video calls, streaming high-definition movies and live sports matches. Netflix and Amazon Prime are tenaciously competing for our precious and scant attention by providing us with increasingly better shows and services. However, our patience has also severely plummeted; a five-second delay is enough to force us to pick a side. A five-second delay can cost these companies thousands of dollars, if not more.
Bear in mind that the bandwidth is limited, but in the last decade, the number of Internet services occupying it have skyrocketed: mobile, broadcasting, space research, telecommunications, Global Positioning Systems (GPS), meteorology, environmental monitoring…. the list is endless. Therefore, to satisfy our ever-increasing demands for speed and availability, we devised another channel, exclusively dedicated to video calls and streaming high-definition videos. This channel of frequencies is known as the Ka-Band and it is on what satellite Internet’s trades occur.
Implementation
To implement the technology, we require only three things: a satellite, a transceiver or an antenna installed by the subscriber to communicate with the satellite, and a modem that will connect the subscriber to the Internet.
Geosynchronous
The satellite is geosynchronous, meaning that it surveils a single patch of Earth. The satellite achieves this by rotating at the same speed as the Earth does. A geosynchronous orbit can only be achieved at an altitude very close to 35,786 km, and to sustain it, the satellite must race at roughly 3.1 km/s. The satellite communicates in the Ka-band of radio wave frequencies, which span between f18.3-30 Ghz. Remember that the satellite is only dedicated to broadband applications.
On the ground, the subscribers either install an antenna dish that communicates with the satellite directly or the satellite communicates with what are called gateways. These are small base or ground stations, the Internet Service Providers (ISPs), that receive and relay the radio signals wirelessly to the subscribers in their vicinity, very much like a sprinkler. The subscriber’s antenna feeds the signals to a modem, which demodulates them into Internet Protocol (IP) packets, thereby connecting him or her to the local network, to the internet.
The Pros And Cons
Now, because satellite Internet is a line-of-sight technology, it does not have to worry about obstructions like mountains and buildings. However, the focused or concentrated nature of this technology means that only a small patch of the Earth can be serviced by the narrow beams. Moving away from this patch impairs reception or coverage dramatically. Numerous satellites in concert could do the trick; in fact, with wireless Internet available virtually everywhere, optical fibers might become redundant in the future.
However, satellite Internet is quite expensive. This is why it has been employed only by huge business corporations. The WINDS satellite, which was launched on February 23, 2008, while does provide broadband Internet services to residents of Japan and the Asia-Pacific region, it is more benevolent to businesses, offering them connection speeds up to 1.2 Gbit/s. This is because residents, unlike business corporations, cannot install antennas with multiple meter-long apertures. Similarly, only Ivy League airline brands like JetBlue, Virgin America and Emirates have been able to afford in-flight Wi-Fi, which is also based on satellite Internet.
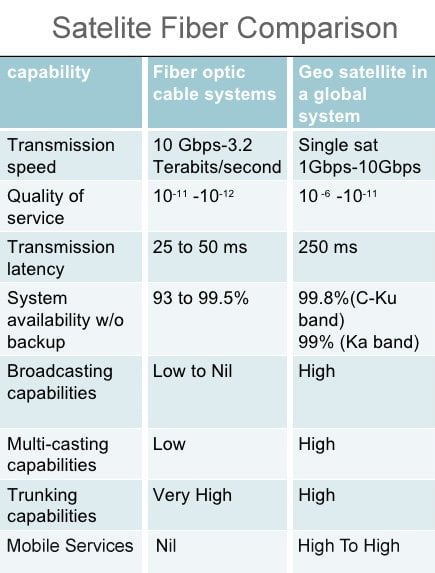
Wires are here to stay, at least for a few more years, because satellite Internet’s functioning is also impaired by rain and weather. This is called rain fade. Wires are also still more optimal for the simple reason that they are definitely faster. The signal between a satellite and the subscriber must travel thousands of kilometers… twice; there is bound to be a delay between the mouse click and the website acknowledging it and granting access to the subscriber.
Yet engineers persist in touting satellite Internet to be the “wave of the future”. They believe it will eventually reign, as innovations have already mitigated rain fade and some experiments have shown that satellite Internet can be 50 times faster than a DSL connection. Only time will tell!