Table of Contents (click to expand)
Hackers do this through various methods, including the use of phishing pages, malware, brute forcing or accessing users’ passwords through other means.
As a kid, I was always fascinated by the idea of passwords. I thought of them as mystical, powerful words or phrases that let me access all my secret vaults. Obviously, those “secret vaults” were common email services that most people have to sign up for. In other words, there was nothing particularly fancy about those vaults.
However, in the world we live in today, it’s virtually impossible to access any digital service without using a password.
Service providers, in a bid to ensure that your personal data and information is protected, urge you to use strong passwords. To add another layer of security, they limit the number of incorrect password attempts you can make (usually 3 attempts).

Despite such security measures being in place, we often hear of cyber attacks wherein hackers leak the passwords and personal data of thousands of users of an app/website/online service.
If there is a maximum limit to the number of incorrect passwords (usually three incorrect attempts) that you can try, then how do hackers, who don’t have the slightest idea of people’s passwords, gain access to so many accounts?
As it turns out, hackers can employ a number of techniques to make that happen.
And you’d be surprised to know that in most cases, hackers don’t have to ‘guess’ your passwords at all…
Recommended Video for you:
How Hackers Figure Out Passwords
Phishing
Phishing is a notorious, yet very common method of acquiring absolutely accurate login credentials of a user. In this method, you (the user) will be contacted by an email, text message or even telephone call, and will be asked to provide sensitive data, such as passwords, banking information, credit card details or personally identifiable information—all of which could potentially give them access to your account.
A very common phishing device is email. One fine day, you may get an urgent email from your “bank”, informing you that there is unusual activity on your account, and that you need to check that everything is alright by signing into your bank account through the link provided in the same email.
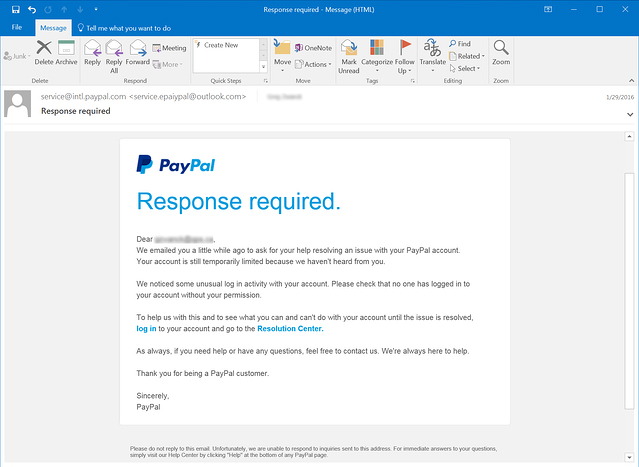
When you enter your login credentials in the webpage that the email leads you to, they get copied and become visible to a hacker who sent you the fake bank email in the first place.
Your username and password have thus successfully been stolen.
Did you see what happened here?
The hacker didn’t have to attempt to enter your account with an incorrect password even once; you gave them your login credentials on a platter.
Malware On Your Device
Another common method of getting a user’s login info is installing malware on their device (laptop, computer, smartphone etc.).
Malware installed on your device can recover passwords that you have saved on your browser. It can even track your keystrokes and obtain your login information through that sneaky approach.
As you can see, even in this method, hackers don’t have to actively steal your password; their malware does that for them.

This is why it’s highly recommended to have a good antivirus program installed on your system and avoid ever using suspicious software and websites.
Password Spraying
This is a kind of attack in which a hacker attempts to access a large number of accounts using only a few popular passwords. What this means is that a hacker doesn’t try to hack one account with a lot of password attempts, but instead try to hack into many accounts with just a few, very commonly used passwords.
If you look up “most common passwords” online, you will see that a vast majority of internet folks still use “123456” and “password” as their passwords.
Why?
Because 123456 is easy to remember.
So, if you’ve used a weak password on one of your online accounts, a hacker will be able to gain access to it without trying multiple times.
External Factors
Bad Website Security
Your strongest passwords are only as good as the website on which they’re used. The security of websites may be poor enough that a targeted hacking attempt can compromise the sensitive information of all its users.
Although major websites (whose user base runs into the millions) usually don’t have this problem, this is something to consider when a website asks you to sign up and provide sensitive data.
Customer Service
Sometimes, a hacker that is particularly interested in targeting you may gain access to your account by calling a customer service helpline and obtaining your login information from there.
However, most well-established internet companies and organizations have safeguards in place to prevent this. This is why you always hear the phrase “never share your login information and password with our customer service executives during a call.”
These are some common methods by which someone can get access to your account without entering an incorrect password even once. The best way to protect your passwords is to only use legitimate software, applications and websites, and avoid using the same password for all of your logins. And yes, perhaps most importantly, create strong passwords!