Table of Contents (click to expand)
End-to-end encryption is a very powerful feature that basically codes your messages. When you send a text to a friend, it gets scrambled (and hence encrypted) on its way and can only be decoded on the recipient’s device. The same algorithm applies for sharing files and making calls. The benefit of such scrambling is that it keeps your chats and calls protected against unwelcome acts of privacy breaching by a third party.

It may be hilarious when you see a meme like that turn up every time there’s a debate about privacy and how it’s being encroached online, but things get a lot more serious when that feeling finally hits you with full force… that Orwellian feeling telling you that:

Whatsapp, one of the most popular communication apps, with more than a billion users around the world, recently rolled out an ‘end-to-end encryption’ feature that will be applied by default on every host device after they are updated next. While most of us were happy about the fact that our texts and calls on Whatsapp would now be ‘shrouded’, there still isn’t much explanation about what the feature actually is and how it does what it claims.
So let’s decrypt this encrypted tech mystery!
Recommended Video for you:
What Is End-to-end Encryption?

End-to-end encryption is a very powerful feature that basically codes your messages. When you send a text to a friend, it gets scrambled (and hence encrypted) on its way and can only be decoded on the recipient’s device. The same algorithm applies for sharing files and making calls. The benefit of such scrambling is that it keeps your chats and calls protected against unwelcome acts of privacy breaching by a third party.
What this basically means is that the conversation you’re having with your friends/relatives is read only by them and no one else; not by Whatsapp, not by your service provider, not by your haters, and not even by the government!
How Does End-to-end Encryption Work?
The aim of end-to-end encryption is to code sender’s information (in this case, messages, calls and shared files) in such a way that only the recipient’s device can decode it, making it immune from any external interception. This is achieved by providing only the recipient’s device with the decryption keys that can decode the message sent by the sender. This is where two main types of keys enter the picture of encryption: public keys and private keys.
Public Keys And Private Keys
The term ‘public key’ refers precisely to what it sounds like, only in the world of encryption, it’s a complex code instead of a physical key made of steel. Anyone can generate public keys (and private keys) on their devices. To better understand what I’m talking about, take a look at what public keys and private keys typically look like:

As you can see for yourself, these keys are incredibly complex and almost impossible to make any real sense out of with just a cursory glance. That’s why there are algorithms and systems in place that do the technical toiling for you in the background while you tap away on the screen of your phone.
When you first register yourself with Whatsapp by installing it on your phone, a bunch of Public Keys for your phone are generated and stored on Whatsapp’s server and are then used to encrypt texts that someone sends you. The number of Public Keys assigned to a device can vary for different apps and programs. In the case of Whatsapp, for example, there are three public keys, namely the Identity Key, Signed Pre Key and One-time Pre Key (this one is used only for the first time someone texts you and is then deleted afterwards).
Here’s how you can understand this process in simple words; when someone, say, Sam, sends a message to Emma, Sam’s phone uses the Public Keys of Emma’s phone to encrypt the message and deliver it to Emma. However, the system has to make sure that the message can only be read by Emma (i.e., the intended recipient) and no one else, not even the server that is relaying the message.
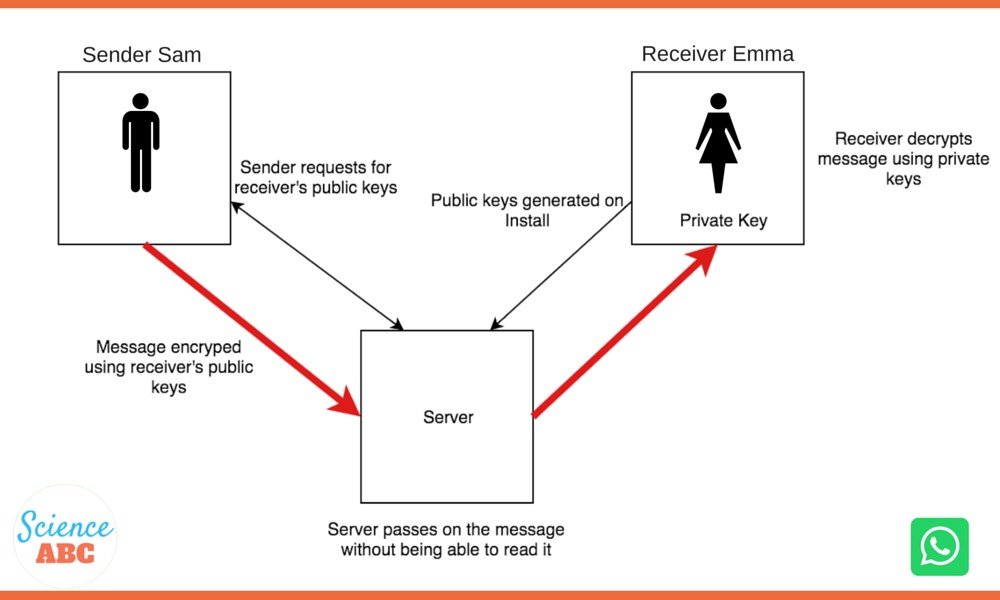
This is where Private Keys enter the picture. Every device has a unique private key that is stored on the device and not anywhere else. Therefore, when Sam sends a message to Emma, it is encrypted and transmitted using the Public Keys of Emma and decrypted using the Private Key when it reaches Emma’s phone.
To give a simple analogy, think of how mailboxes (post-boxes) work. Anyone can put their letters into the box (server) through the narrow slot (Public Key), but only the postman, who has a unique key (Private Key), can unlock the box and retrieve all the letters. Encryption on devices works similarly, but they do it using huge chunks of algorithms and codes.

Note that this is just the basic description of how end-to-end encryption works; for an in-depth explanation of how Whatsapp applies this encryption to host devices, check out the Whatsapp Security Whitepaper.
Pros And Cons
In a world where everything from ordering a pizza to sharing highly sensitive documents is done online, there is an urgent, almost desperate need for tools and systems that are able to safeguard one’s privacy. The need becomes even more pressing in the context of apps that we use on a ‘hyper-regular’ basis, such as social media apps and certain communication apps that feature ‘free’ texting and calling.
With all that being said, the end-to-end encryption feature of Whatsapp is undoubtedly a welcome measure for its users, but like everything, it also has its downside. Since this is a technically sophisticated automated feature that encrypts chats and calls on every device, it gives peace-keeping authorities and governments a tough time keeping an eye on anti-social elements and other nefarious activities.
All in all, it’s a useful feature that marks a significant step towards privacy safety on an end-user level; how it’s going to influence society on a global scale is something that we’ll have to keep our eye on.