Fingerprints are formed when the skin buckles while the fetus is developing in the womb. They are unique because of the many variables that decide how each individual ridge is formed. Fingerprints are used to identify unknown victims, witnesses or suspects, to verify records, and most importantly, as links between a suspect and a crime.
Before I tell you the answer, let’s start by talking about how fingerprints are formed.
Recommended Video for you:
What Are Fingerprints?
Fingerprints are the tiny ridges and patterns on every finger that you have. These friction ridges are present on your fingertips, palm, toes, and soles! They are also known as ‘dermal ridges’. Fingerprints are completely unique to every individual person.
How Fingerprints Are Formed?
The crux of fingerprint formation lies in the field of developmental biology. Our fingerprints reflect the environment we encountered when our life began. A person’s fingerprints are formed when they are a tiny fetus developing in their mother’s womb. The faint lines you see on your fingers and toes were completely formed by the time you were 6 months old – 3 months before you were born!
Scientists agree that fingerprints begin to develop around the 10th week of pregnancy, but no one is certain of the precise process that creates them.
The most widely accepted theory states that the middle skin layer, called the basal layer, is scrunched between the inner layer (the dermis) and the outer layer (the epidermis). The basal layer grows faster than the other two, causing it to strain against its neighbors.
This straining pressure causes the skin to buckle, resulting in the folding of the epidermis into the dermis. This shows itself in the complex ridge patterns we see on our fingers today. Ridges are the faint lines on the fingertips that create the foundation of a fingerprint.
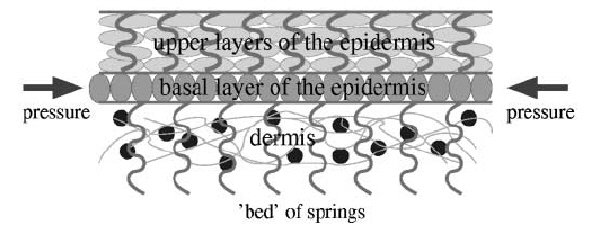
It is precisely because the pattern is encoded at the interface between the dermis and epidermis that it becomes nearly permanent and cannot be destroyed by superficial skin injuries. Having said this, the ridges of fingerprints are particularly susceptible to wear.
Can You Alter Fingerprints?
Repeated activity, such as bricklaying, can wear down fingerprints, rendering them inadequate for personal identification. Likewise, some criminals purposely burn off their fingerprints, either with acid or fire, in order to let them move through the criminal world like a ghost. However, in most cases, due to the imprinting of fingerprints in deeper skin layers, once exposed to the abrasive, caustic or hot conditions cease, the fingerprints will eventually grow back.

Why Are Fingerprints Unique? Can Identical Twins Have The Same Fingerprints?
Fingerprints are set in stone by the time a fetus reaches 17 weeks. Fingerprint pattern formation consists of two components: developmental and genetic. The ridge pattern development not only depends on genetic factors but also on unique physical conditions. So even if identical twins are genetically similar, the pressure faced by the fetus in the womb can affect their fingerprints. Even the difference in the length of umbilical cord can make changes to the fingerprints. So ya, identical twins could fool everybody with their looks, but they ain’t fooling the fingerprint test!

Innumerable environmental factors are thought to influence the formation of fingerprints, including blood pressure, oxygen levels in the blood, nutrition of the mother, hormone levels, the exact position of the fetus in the womb at particular times, the exact composition and density of the amniotic fluid that’s swirling around the fingers of the fetus as they touch surrounding structures, and the pressure with which they touch their surroundings. These myriad variables decide how each individual ridge is formed.
The level of activity of a fetus and the general chaos of the conditions of the womb prevent fingerprints from developing exactly the same way in any two fetuses. The entire development process is so chaotic that, over the entire course of human history, there is virtually no chance that the exact same pattern formed twice. What this means, though, is that fingerprints are different on every finger of your hand, they’re different on the same fingers of opposite hands, and even the fingerprints of identical twins are different from each other.
Are There Any Applications For This Unique Quality?
Identification Of A Suspect In A Crime
One major use of fingerprinting is related to criminal investigations. Formed by a combination of the sweat and oil from the skin coming between the fingertip pattern and a surface, fingerprints can often be used to identify the perpetrator of a crime. Fingerprints are used to identify unknown victims, witnesses or suspects, to verify records, and most importantly, as links between a suspect and a crime.
Even when there is no suspect in a crime, fingerprints can help develop leads and provide clues about the criminal’s size, sex, and occupation. Small prints tend to be made by smaller people, while fingerprints on a wall indicate a suspect’s height. Even the absence of prints may be a key factor. Suicide scenes, for example, should never show any signs of attempts to wipe prints away.
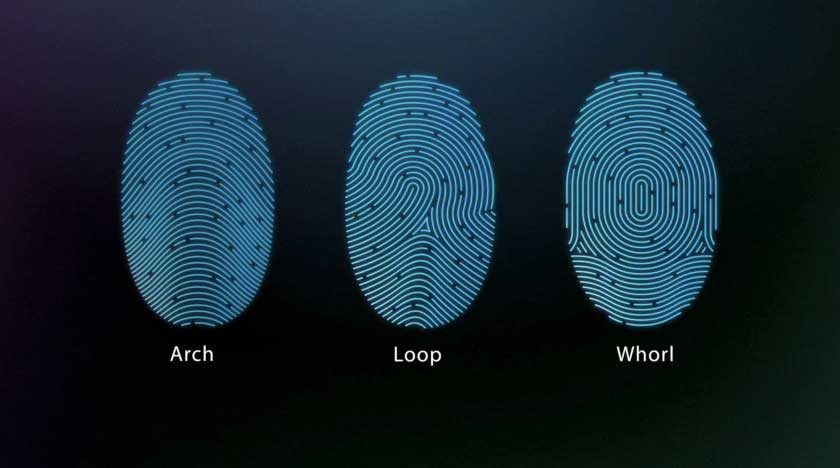
For classification purposes, experts divide fingerprint ridge patterns into three basic classes: Arches, Loops, and Whorls. Each class can be further divided into numerous sub-categories. Fingerprints also show slight racial variation. People of African ancestry tend to have a multitude of arches, people of European background have many loops, and those of Asian descent have a fairly high frequency of whorls.
Dactyloscopy
Known as dactyloscopy, a system of fingerprint identification was developed from the work of Sir Francis Galton by Sir Edward R. Henry. Nowadays, fingerprinting is used across the entire world and has many valuable applications. Between the years 1901 and 1910, many countries began using fingerprints for identification. In 1924, the Identification Division from the FBI, in the USA, started using fingerprints for identification.
A Word Of Caution
However, something that needs to be remembered is that several factors can contribute to inaccurate identification. First of all, no two fingerprints or impressions are precisely alike. Second, fingerprints collected at crime scenes are often imperfect and are frequently either partial, smudged or dirty prints. Third, at some point, people are involved in the identification process, which leaves the entire system open to human error.
In other words, even fingerprint examination is not a foolproof way to identify a person, particularly if that person is actively trying to fool you!













